Rebuttal to Pen Test Partners

As typically happens when sex toy related news hits, my phone began pinging incessantly as half of the Internet sent me a link to this Motherboard article about hacking the Svakom Siime Eye. The Siime Eye is a vibrator that has a camera in the end of it. It uses Wifi to stream video or still pictures to your mobile device. It's been on the market since 2015.
Reading the article made me feel somewhere between disappointing and angry for a variety of reasons.
The first of which was that I just ordered a Siime Eye off Amazon literally a week ago and it is due to be delivered in the next day or so. I had already gone through the app and manuals and knew of a lot of the issues they mention in their report, but now it felt like the expense was wasted.
However, what really bugged me was the tone and slightly juvenile and offensive way both the article and report approached the topic.
Needless to say, that while the article and the associated report were technically correct, I felt they did alot to undo the work of the IoD project.
If you read anything on this site, the twitter account or otherwise associated with the IoD, you'll find that a great deal of effort has been spent to be non-judgemental and non-discriminatory as well as gender and sexually neutral. I make no judgements about with whom, how, when or where anyone's usage of these devices (though what does bring up some interesting questions). It's a basic fact of life that people have sex and people masturbate. While you may not agree with details about both, I would hope you agree that everyone deserves to have privacy and security in the products they buy and use. If you have any sense of humanity, you don't want to see harm come to anyone and if you do, well, you're just sad.
First off, the article and report both deal with the fact that yes, it's a vibrator with a camera in it. (I admit to being a bit surprised when I came across it in my research, but as said, I don't judge). The article takes a barely contained juvenile tone of incredulity that people would want to use such a device.
If you're using an internet-connected vibrator equipped with a camera that allows you to stream your "pleasure" right to the internet, your intended viewers might not be the only ones watching.
Its been on sale over 2 years, so I assume there's enough of a market to support it. Whats the big deal?
My issues with the article stem from the behaviour of those interviewed for it and the contents of their report.
First off was the researchers chosen nome-de-plume of 'Beau de Jour' (Broken french for 'Beautiful Day') which was probably an attempt to make an allusion to 'Belle de jour' (Beauty of the day), another name for prostitute (or trying to invoke a well known authors pen name). Considering that the listed staff of Pen Test Partners is entirely made up of men, this seems a bit misogynist and inappropriate to me. At the very least, feeling like you have to hide behind a pseudonym because you're researching sex-tech shows immature attitudes towards sex.
The article also refers to the device as "streaming right to the internet". While it does stream video from the device to the app, it only records it locally and does not "stream" it outside of the local device. You have to upload the saved video somewhere in order to be viewed on the internet. This makes it far from "live". Now it's not impossible that one could write your own software to receive the stream over Wifi on your phone and reflect it out to the Internet over LTE, that functionality is nowhere in the included software.
Looking through the report and all the "discoveries", so much was presented for sensationalist reasons. It was designed to make a splash in the press, but was lacking context that made many of their issues and findings almost moot.
Lets go through some of them.
Default WiFi password
The Siime Eye acts as a WiFi access point and has a default network key of '88888888' built in to the app and firmware (it's also in the app instructions and the manual). The user can change the password to one of their own choosing, and is actually encouraged to in their apps connections instructions (Item #5):
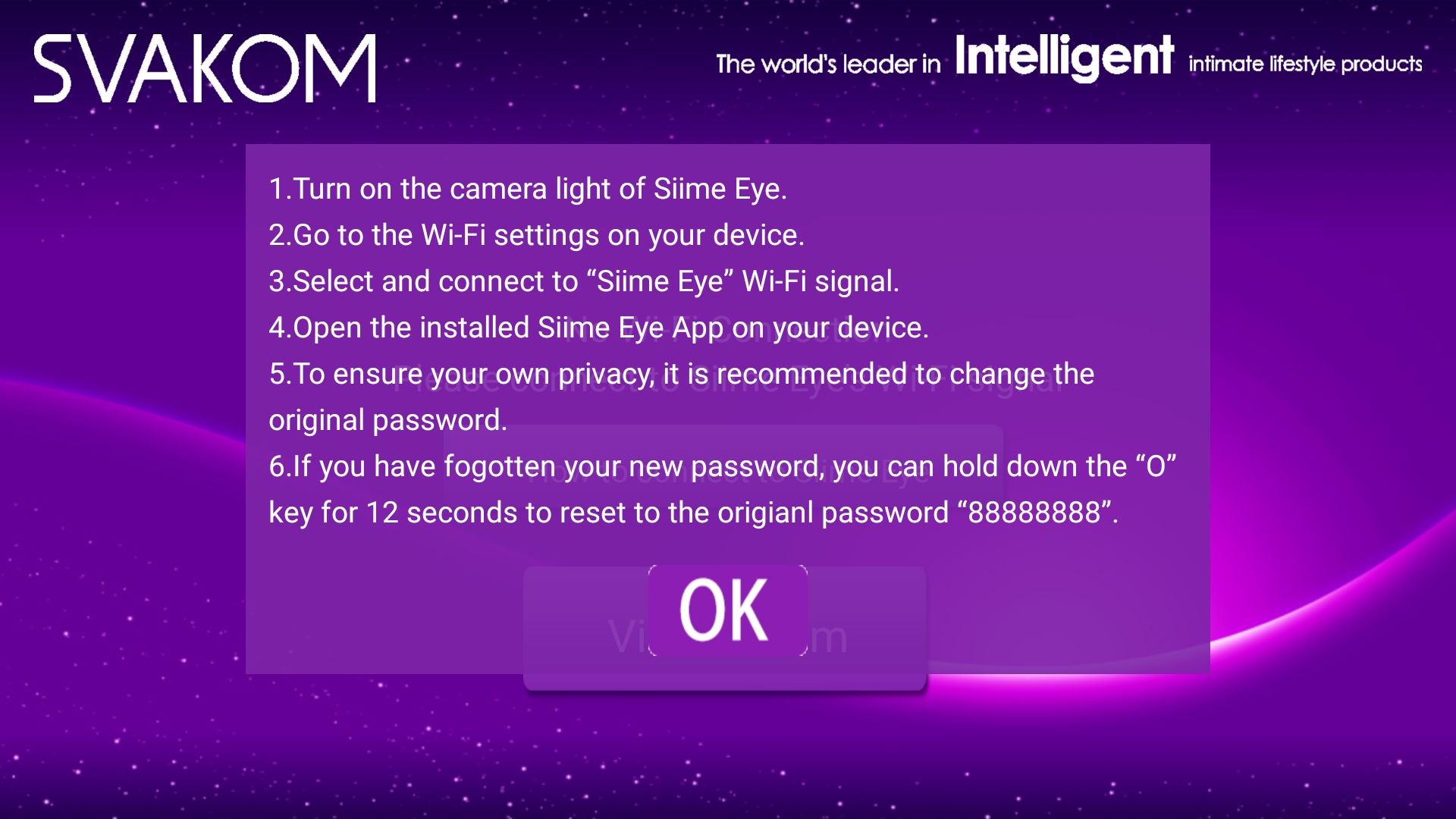
Performing a reset on the device resets to this default. This actually in many ways is better than defaulting open. At least the traffic is encrypted, even if it's a known value, as opposed to in the clear.
"The fact they chose to use Wi-Fi was utterly stupid"
Founder Ken Munro's comment that Wi-Fi was a stupid choice shows to me that he didn't think about this very much. For the device to meet its design requirements, there's not much choice in terms of protocols. Every modern phone and tablet have WiFi, and Bluetooth does not have the bandwidth for video or large picture transfers with any speed. I'm curious, were he designing the product to meet the design requirements, what he would have chosen? Once you grow up and get past what the product will be ultimately be used for, it's simply an engineering issue. Given what the product designers were attempting to accomplish, WiFi is a sane choice (some implementation issues not withstanding).
In addition, the device uses WPA encryption which is what nearly all home WiFi are protected with. If you trust it on your home network, it should be robust in this situation, provided you choose a decent password. Like so many security systems, if you don't change the default passwords or choose poor ones, it's going to come and bite you regardless of what kind of device it is. You can only engineer out a certain amount of stupid.
"THAT WEB APP SERVES THE VIDEO FROM THE CAMERA! OMG!"
As above, put yourself in the shoes of the designer. You've been given the design requirements to build a vibrator with a camera. Until now, everything you've designed has been analogue, and 'manually' operated. You may be a good materials engineer, or electrical engineer, but you've never had to deal with connectivity before. No one has until very recently.
The design means you need something with wireless connectivity, small size and weight, and a method for streaming video to a mobile device. Instead of trying to engineer something yourself, you look to existing products, or at least parts of products. Strip away the propellers, motors, and chassis of one of the many consumer drones on the market and you have literally dozens of variations on a small, lightweight, mobile streaming WiFi camera. Why re-invent the wheel, especially when you have never designed a wheel before.
(note: a vast majority of Wifi camera drones operate open, without Wifi security)
Once again, if you get past the intended use of the device and look at it from an engineering standpoint, it makes sense (implementation issues aside). Such re-purposing of subsystems happens a lot in the electronics industry.
Geo-locating wireless vibrator users
This one pissed me off because if you peel back the layers, just a bit, you see that their breathless warning doesn't hold any water.
The report claims that since the device has a static SSID of "Siime Eye", its possible to "wardrive" (scanning and mapping wireless networks while in motion) to detect where these devices are. While this is true, and I have yet to receive mine to do any range testing, the risk is overblown.
As proof of the danger they point out that sites like wigle.net which catalogues wardriving data, has entries for "Siime Eye" and point to out with a graphic, one located in the middle of Tokyo.
Problem is. That's all there is.
I checked the Wigle.net database for "Siime Eye" networks and found exactly two.
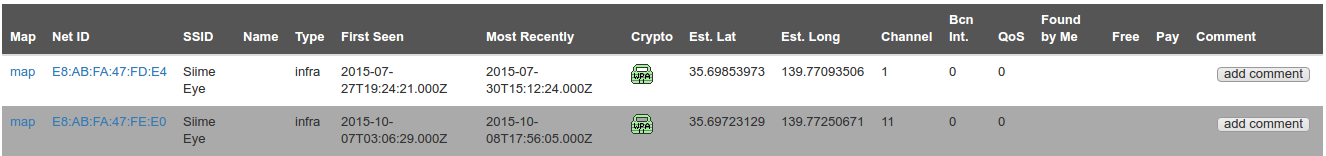
They were detected in July and October of 2015, which is around the time of release to the market. Both were located in the same place in the middle of Tokyo which is unusual if these were "in the field" devices being used by customers.
A few moments of investigation that was not taken by the researcher or the reporter revealed a very likely answer that undermines their dire warning.
The location is right in the heart of the Akihabara area of Tokyo. An area that is famous for it's giant electronics stores that seem to sell literally everything. This would likely include sex toys of all shapes and descriptions.
The most likely explanation then for these two devices is that they were demo units in one of the stores and were not in actual use as intended by end users.
So out of 327,235,207 networks observed (as of writing), only two devices have ever been discovered, and they were in a place that intentionally put them in front of a thousands of shoppers per hour. Kind of the opposite of the expected usage scenario when you think about it. The fact no other has been detected says to me that your chances of being detected with one is more likely to be from the buzzing sound coming through thin walls than by being detected via WiFi.
(Note: When I receive mine, I will do some range testing to find out the average detection range and update accordingly. I expect it to be very short range)
"From that, we can assume that there’s functionality in the Siime Eye to send emails, change DNS settings, and even add a Skype account"
(To preface this section, I have not tested mine yet and cannot verify everything. However analysis of the software and the researchers own report can allow for some educated guesses.)
Since we've established the likelihood that engineers re-purposed a drone camera system to shortcut the development of the final product, we can explain the extra functionality.
I completely agree that leaving all the extra and unneeded functionality in the device was sloppy and a waste. However, much of this added functionality that they point out as potential privacy risks are complete non-starters.
Note the usage of assume in "we can assume that there’s functionality" when mentioning email, network storage and skype settings. They fail to mention that, even if these functions (send email, write to network storage or connect to skype) were completely implemented, the device is still an access point, not a client. This means that devices connect to the Siime, much like you connect to your home router, not that the Siime connects to other networks. In simple terms, there's no way for the Siime to get Internet access. So even if it had functionality to send emails, files or connect to skype, there's no way to connect to the internet. The data basically can't leave the device. The only thing that can is the data being requested by the client device and the mobile app.
This information was included without any context and appears to be threatening when it's really not.
That said, there may be some situation where a phone or laptop is dual homed, connected to the Siime and the internet through two connections and they are bridged. Even then, there is nothing really to ex-filtrate except the video stream. To do that, all you need is the client app or software to view the feed if you are able to connect to the device. It's such an edge case as to be safely ignored.
Disclosure timeline
Having reached out to many IoD vendors, I know that sometimes it can be difficult to get a response right away. This is an industry that doesn't realise that they are software vendors now and dealing with connected threats, both things they've never had to deal with before. As a result, they generally don't have any direct method to report security vulnerabilities to those that understand them. Usually it's a single customer service email address or media contact email that goes to non-technical people. It can take some work and repeated tries through different channels to get their attention.
(Note: A major part of the IoD project is to help vendors to establish such communications channels and internal programs to deal with such reports)
Pen Test Partners don't seem to have any grasp on this and is applying a standard that would work with Google or Microsoft, to companies who have no idea what they are involved in or are small companies with limited resources. In addition, Pen Test Partners made some very poor decisions in their disclosure timing that seemed to setup Svakom to fail.
24/12/2016 – Svakom Informed about web interface issues. No response.
Take a look at the date. They sent their first vulnerability report to them on Christmas Eve (Which was also a Saturday)! I don't know about you but I tend to take the week between Xmas and New Years off and come back to a giant pile of email. One can understand how a non-technical staff member (which is likely who it was at the other end of the customer-service@svakom.net email) would miss it or not understand and dismiss it.
09/01/2017 – Follow-up email sent to ask for some kind of response. No response.
One advantage of working with vendors in this industry is that you learn things about how the industry operates and what is going on behind the scenes.
January is conference season for the adult industry. Almost the entire month is taken up with conferences and tradeshows. The Xbiz show (a major B2B tradeshow event), and the AVN awards are the two big shows going on, right smack when the second email was sent. For these events, it's usually all hands on deck since making distribution deals and other contacts can make or break a business (many vendors are smaller than you'd think).
So again, a non-technical person at the end of a general delivery email address may miss the second email in all the chaos that the season contains.
09/02/2017 – Svakom informed of further code injection issues & intention to write a blog post. No response.
Again, who's receiving it? How was the email written? Was it human readable or just meant for techs?
Obviously the message didn't get through, but before you give up, in this day and age, it's not like there aren't other options for communications. Why not take 5 seconds and try Twitter? Their website also has a good old phone number. Sometimes a personal touch helps. Calling and explaining the situation and asking to be directed to a technical person can work wonders. It doesn't take much to try.
What about reaching out through a well connected project about hacking sex toys? (hint: me!). It's a small industry overall and it's likely one of my contacts at a partner vendor knows a more direct line of communication you could use. They may be able to provide and introduction.
Pen Test Partners can't even claim that they don't know about the project. I spoke with Ken Munro at Defcon and invited him to help me when I was starting the IoD project. As well, one of the Pen Test Partners consultants (@Cybergibbons) follows the IoD project on Twitter
I find it hard to reconcile this half hearted attempt at communication with their claim to take "every effort" to establish communications from their disclosure policy:
"Pen Test Partners will make every effort to establish confidential communications with the vendor. This may involve using the vendor’s published email address if no security contact is publicly listed."
So instead of of holding everyone who puts together an IoT device to the same standard as Microsoft or Oracle, maybe Pen Test Partners should look at the industry the vendor is in and attempt to understand it a bit before applying one size fits all. If they want to actually increase security for their customers, this is alot more effective.
Conclusion
While the Siime device has some serious issues that need to be addressed no doubt, Pen Test Partners decided to use the juvenile "OMG,SEX!" angle of hacking a sex toy for some cheap publicity. By being unprofessional, sensationalist, and sexist, they have only succeeded in hurting the efforts of the IoD project to build meaningful bridges with the industry and providing real change and improvements to security.
Instead of going for the cheap win and free PR, I invite Pen Test Partners to join with the IoD project to help create a lasting change in the adult toy industry. By working together to help educate and provide some of the much needed knowledge and specialised consulting to vendors, we can raise the bar of security forever across a whole industry.
So what will it be? Cheap PR and misogynist jokes, or aspire to a higher ideal that has a direct effect on the safety, security and privacy of the public long into the future?
