Bad vibes? Or: Why you shouldn’t trust everything you read on Reddit

Note from RenderMan: This post is a writeup by a friend who specializes in malware analysis and tracking who wishes to remain anonymous but wanted to share what they found. More than happy to post such things, so feel free to reach out if you want your research posted anonymously.
On February 17th, Reddit user /u/VegetableLuck posted a possible infection to the /r/Malware subreddit:
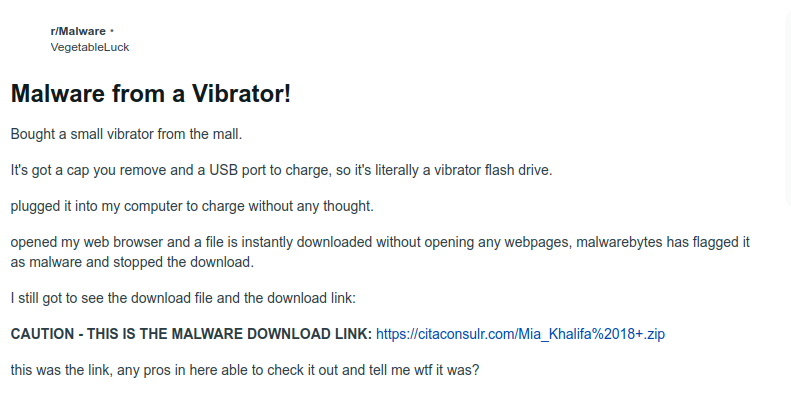
Malware? From a vibrator? As many of you who had seen the original post might know, speculations ran wild - from the (expected) jokes about remote control vibrators and quips on penetration testing (never heard that one before), the community was in general amusement about the possibility of internet-transmitted viral diseases… so to speak.
According to the user, they purchased the device in question at Spencer’s, a popular novelty shop more famous for its pop culture shirts, cheap lingerie, and rampant theft problem than for malicious vibrators. They likely paid a touch more than they should have, given that the device was dropshipped out of Aliexpress.
So without getting too deep into possibilities and ‘what-ifs’, to be addressed later, let’s talk about the data we had available: the download link.
The sandbox
Of the more helpful commentary was a set of sandbox results from /u/hipsherdominic that provided insight into what the user may be seeing. The link that was downloaded led to a .zip file, helpfully and appropriately named ‘Mia_Khalifa 18+.zip’, unpacking to an .msi file.
The file has some pretty obviously bad vibes from the get-go. Upon execution, the .msi file makes a series of connection requests out to domains like:
- https://gemcreedarticulateod[.]shop/api
- https://secretionsuitcasenioise[.]shop/api
- https://claimconcessionrebe[.]shop/api
- https://liabilityarrangemenyit[.]shop/api
Note the commonalities between these domains: they are all a random set of dictionary words with misspellings or extra characters at the end of the string. They are all shop TLDs, and they all point to the /api uri. They also are using SSL/TLS.
Next, we look at the data sent. In the decrypted packet capture, there’s a callback to the C2 (Command and control server) of `act=life`. The network communications also include a few questionable IP callouts, like http://176[.]113.115.227:13633/473ef .
This IP is notable because it’s been seen on past malware campaigns, specifically in cracked software being spread on YouTube.
These are all rather strong primary indicators of an information stealer known as Lumma. Lumma is an information stealer regularly promoted for sale on Telegram and Discord with a range of prices based on featureset. A malicious file is usually embedded with a download script by the purchaser, to be executed by an unlucky downloader. This information stealer also has a built-in anti-sandbox method - it uses mutex values to detect sandbox components. This can make analysis a lot more difficult if sandboxes aren't configured with anti-fingerprinting measures
Lumma’s command-and-control is performed through a hefty trickle of information to the domains listed above, usually including anything from browser profiles and extensions to passwords and cryptowallets.
So what?
By this point, some of you may be asking about the big vibrating elephant in the room: “How did this get on a vibrator?”. The answer is, quite simply, that it didn’t. After a long thumb-twiddling session awaiting the arrival of the vibrator in question, we chopped it open and found…
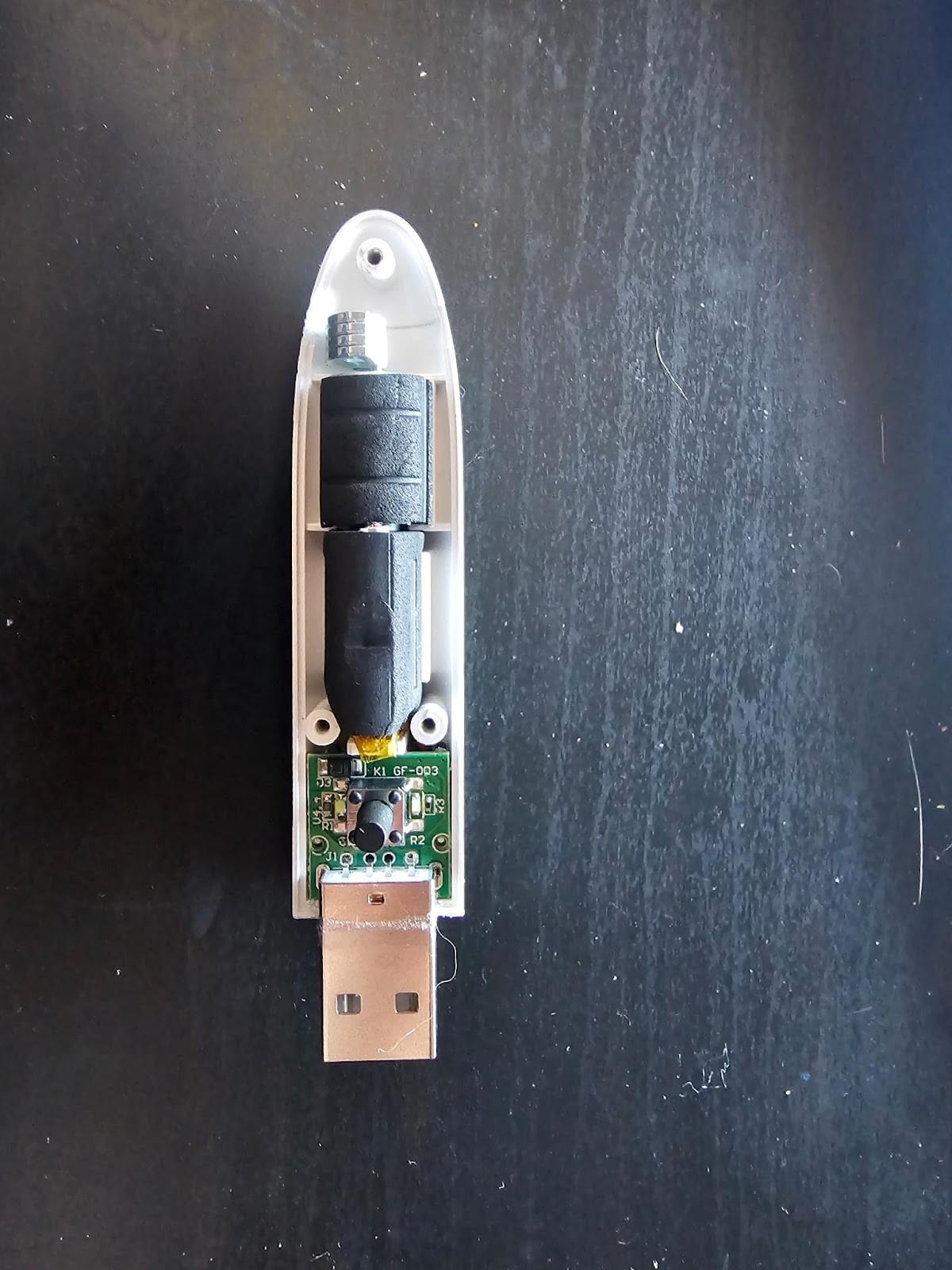
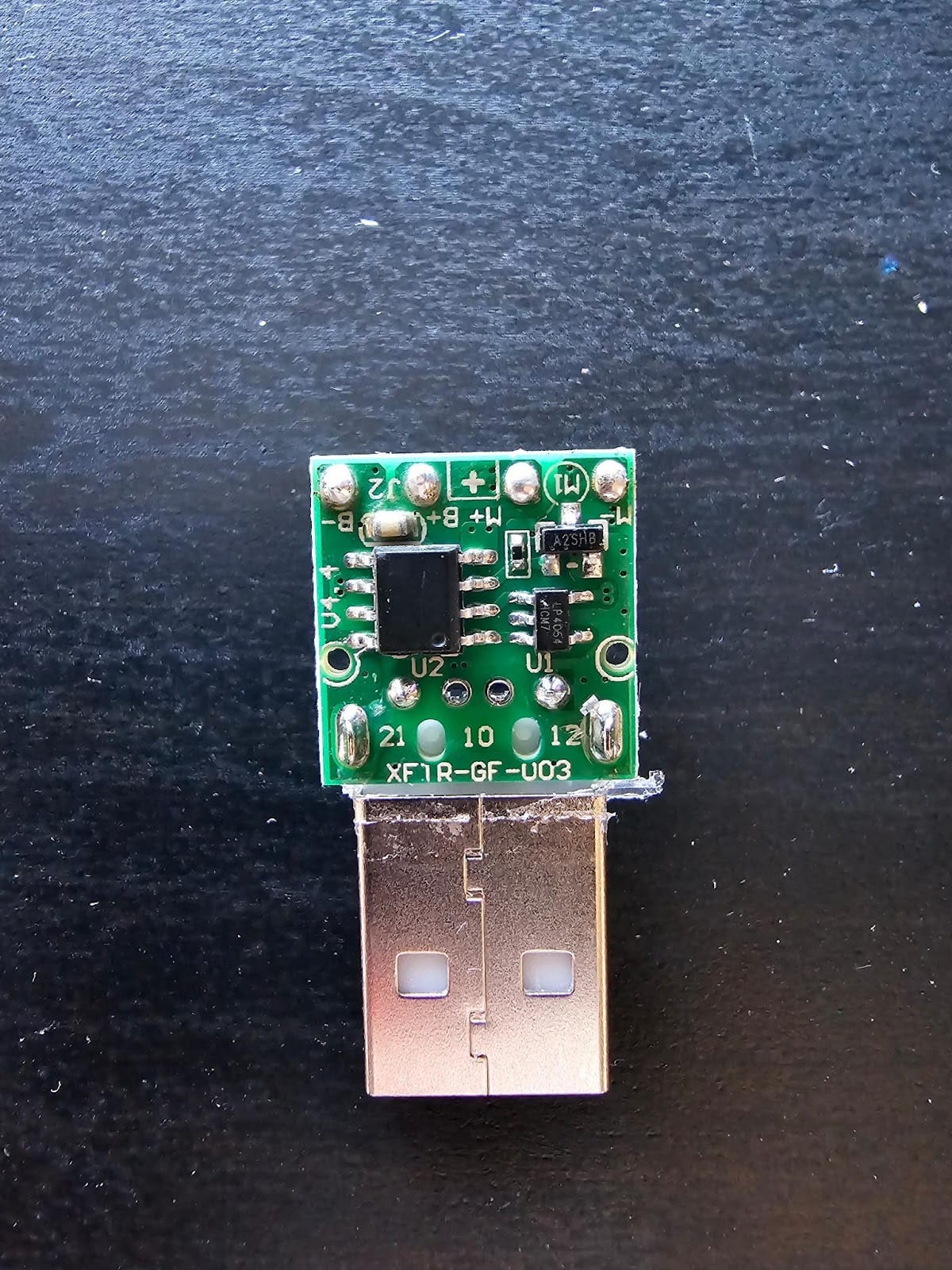
Nothing!
Here’s the thing about cheap drop-shipped items: they’re cheap. The features on this particular ~$10USD vibrator didn’t include anything internet connected, USB storage-related, or fun in a malicious sort of way. That board you see is a voltage regulator for the battery pack just above it, which powers the (actually pretty powerful) motor just above it.
The likelihood of a vibrator having USB storage capabilities at this price is low. The likelihood that the same vibrator would have firmware-embedded malware is lower. And the likelihood that this USB storage device-cum-malware delivery vehicle (pun intended) would be sold for a low price at a major retailer is lowest.
Note that we don’t say it's impossible, which is part of the reason why this examination is coming out now and not a few weeks ago. When inexpensive electronics are made, they tend to be crafted with whatever usable leftover parts are lying around, not with custom boards and crafted features from the manufacturer. So there was actually a tiny possibility that an old USB storage device would find its way into this design. Note that the user did indicate another device was plugged in at the time, but with identical features - we consider it extremely unlikely that this device was an exception to the cheap cost rule.

In conclusion
The most likely possibility is that poor /u/VegetableLuck picked up this malware through a piece of cracked software that was posted on YouTube. It may have already been running for a while before the user noticed, or it could have executed while they were at the keyboard.
If we did learn something from this it’s the following:
- Don’t trust Reddit. No one in the comments section suggested that the malware may not have come from this device.
- We should not plug in unfamiliar devices into our anything. You don’t know where that’s been. USB condoms exist for a reason.
- We really want to see a USB storage device-cum-malware delivery vehicle PoC. That’s not an invitation for malicious use, just an invitation to make a Frankenstein’d vibrator that also delivers malware. A vibrating virus, if you will. If you do happen to make a vibrating virus, let us know. We’re into that.
- Occams razor (the simplest explaination is often the truth) applies very well here. Is it an effort, either intentional or unintentional to infect the vibrator users of the world, or a simple case of causation being confused with corellation? The user was most likely infected or noticed the infection obtained elsewhere around the time they plugged in the vibrator to charge and then assumed the two events were related and paniced and ran to tell Reddit.
