Destroying the Reddit Lovense Remote Vuln Conspiracy


So much writing needs to be done, I can't keep up. Far too much uninformed research and just pure conjecture to keep up with.
Basically, something could be the most boring thing on the planet, but the moment it's associated with sex, it's a sensation. Humans are weird.
On Friday, Nov. 10th, twitter lit up to let me know about a new thread on Reddit entitled "PSA: Lovense remote control vibrator app recording "private" sessions without express permission" that breathlessly described the shock and horror of... Well, you can read it for yourself:
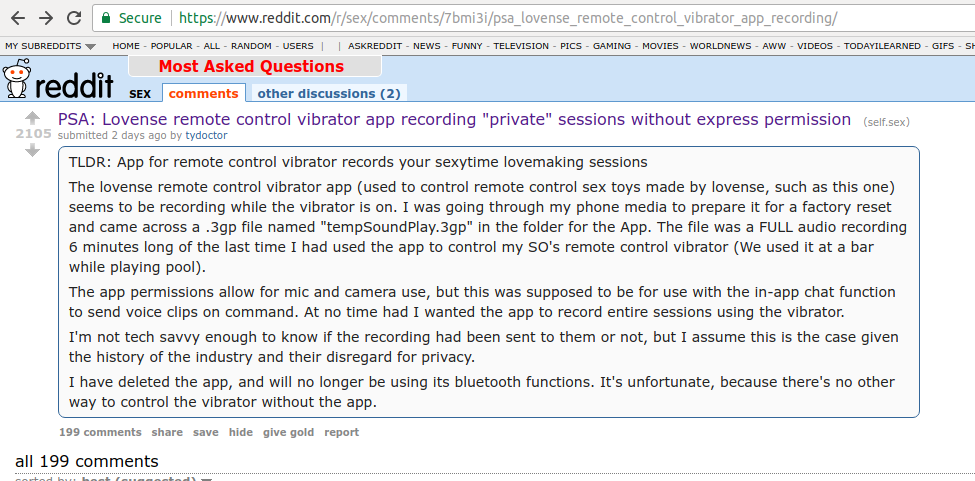
TLDR: App for remote control vibrator records your sexytime lovemaking sessions
The lovense remote control vibrator app (used to control remote control sex toys made by lovense, such as this one) seems to be recording while the vibrator is on. I was going through my phone media to prepare it for a factory reset and came across a .3gp file named "tempSoundPlay.3gp" in the folder for the App. The file was a FULL audio recording 6 minutes long of the last time I had used the app to control my SO's remote control vibrator (We used it at a bar while playing pool).
The app permissions allow for mic and camera use, but this was supposed to be for use with the in-app chat function to send voice clips on command. At no time had I wanted the app to record entire sessions using the vibrator.
I'm not tech savvy enough to know if the recording had been sent to them or not, but I assume this is the case given the history of the industry and their disregard for privacy.
I have deleted the app, and will no longer be using its bluetooth functions. It's unfortunate, because there's no other way to control the vibrator without the app.
Wow. The amount of FUD (Fear, Uncertainty and Doubt) being spread here is a lot for a short post. I'm sure there are other occasional posts like this that fly under the IoD radar.
Unfortunately, this one got picked up by the Verge who reported the conjecture and uninformed supposition kind of verbatim. To the authors credit, they did try and reach out to Lovense and promised to update the article. Not a lot of chance of that on the Friday of a weekend though....
I was contacted by jolio shmolio and asked to independently verify or refute the Reddit posters claims. I was actually already in the process of doing so but the email was a welcome push to get something done right away.
There were three questions to answer:
- Was the presence of the tempSoundPlay.3gp file reproducible as indicated by some Reddit comments?
- Was this file sent to Lovense or any other parties?
- What was the purpose of the file and why was it there in the first place?
Fortunatly, the IoD project has an archive of various versions of apps for just this purpose.
1. Reproducible?
Using the Lovense Remote v3.0.6 app (last version before the most recent with the fix for this issue) on a test device, it was quickly determined that the file did indeed get created (via the SoundPlayActivity.java file). Any usage of the "Ambient sound" feature would create the temp file in the /sdcard/wear/temp directory. This file was found to persist after leaving the Ambient sound function or closing the app but would be overwritten on the next use.
The contents of the files was found to be a complete recording of the surrounding sounds while the Ambient sound function was in use. Restarting the function or the app would overwrite the file, thus only the last "session" is retained.
There were functions in the app related to cleaning up these temp files (WearUtils.java), however they were not being called properly (see further down)
2. Was the file sent out of the device?
After disassembling the APK with various decompilers, the source was searched extensively and nowhere is that file accessed by any process that sends it anywhere. Additionally, Dynamic testing (monitoring the traffic to and from a device running the app) showed there was never any attempts to move the tempSoundPlay.3gp file.
Feel free to check yourself. APK's are easily decompiled and the source searched for yourself. Feel free to prove me wrong.
3. What was the purpose of the file and why was it there in the first place?
An examination of the source code (of which I will save you the headache of reading) showed that the file is created as part of the "Ambient sound" function of the app. It begins recording the ambient sound of the room and periodically takes a measurement of the amplitude (volume) of the sound in the immediate area. This value is then used to drive the vibration on the device. The higher the ambient sounds, the higher the vibration strength.
While this file could be stored in RAM, it is much easier and more efficient to stream it to disk for temporary storage (500mb of RAM is more useful than 500mb of disk). This makes sense, especially when it was clear that the file was meant to be purged once it was no longer needed.
Analysis of what likely happened....
The Reddit user discovered the file on their phone ("a .3gp file named "tempSoundPlay.3gp") that concerned them. It had the sounds in the area recorded by the phones microphone during the time they used it (The file was a FULL audio recording 6 minutes long of the last time I had used the app to control my SO's remote control vibrator).
They used this information to make a technically correct, but founded in the opposite of what was actually happening: "The lovense remote control vibrator app ... seems to be recording while the vibrator is on")
The user then goes off the rails and confirms that they literally do not know what they are talking about. Allow me to break it down statement by statement as there is much to take apart in this very dense pile.
"The app permissions allow for mic and camera use, but this was supposed to be for use with the in-app chat function to send voice clips on command. At no time had I wanted the app to record entire sessions using the vibrator"
Given that the function the user was using the app, the "Ambient Sound" function, I do wonder about them. Presuming they know that the louder the sounds around them, the more the device vibrated, I would ask a very simple question:"How did you think that the app knew what the ambient sound levels were without using the microphone?". To my knowledge, phones are not telepathic (yet. I bet Google's has a project trying to do that right now).
Android permissions are not that granular. Granting an app a permission for the microphone and camera allows any part of the app to use those functions should it want to. You cannot (though it would be nice to) have granular control of when you want to allow permission in an app or not.
I'm not tech savvy enough to know if the recording had been sent to them or not, but I assume this is the case given the history of the industry and their disregard for privacy.
I'm just not going to touch the first part of this....
As shown, there's zero evidence that the file was going anywhere. I challenge anyone to prove me wrong. Here's the unpacked source and APK I used
The assumption that there was a nefarious or malevolent purpose to the file is an indicator of a great many cognitive fallacies. The assertion that there is a "history" is likely based on the We-vibe case. We've commented on it here before and once you get past the sensational headlines, you realise the lawsuit was a big deal about pretty much nothing. Articles to be posted on this site in the near future will poke a ridiculous amount of holes in other cases of IoD vulnerabilites being malevolent.
In short, the user has no idea what they are talking about and likely didn't want to know.
I have deleted the app, and will no longer be using its bluetooth functions. It's unfortunate, because there's no other way to control the vibrator without the app.
As I think has been shown, the most likely scenario is one of a bug that failed to take out the trash after it was done. Compare this with the idea that there is a secret effort to record audio of peoples usage of these IoD devices for some nefarious purposes.
Occam's Razor kind of applies very nicely here.
Oh, and depending on the device, you can get limited functionality via the on-off button. Pressing it quickly will cycle through the pre-programmed patterns.
Lovense responded quickly and had a fix (that despite the thin information provided) very quickly pushed to users and should be commended. As well, the app has a feature that alerts you when a new version is available to encourage users to upgrade as soon as possible.
Authors Note: I can't imagine the usefulness of Ambient sound recordings of users IoD usage would be of any use to vendors. Have you ever stepped back and listened to people have sex? People make some of the most ridiculous sounds mid coitus, so it's only useful for comedy purposes I think
The Reddit user's first instinct, upon the discovery of something odd, was to run to Reddit to make a highly ill informed post. A simple email to the vendor would have been far more productive and less embarrassing. The media picking up the post and reporting it nearly verbatim and bringing up other IoD vulnerabilities proven to be rife with errors and half truths just adds to the problem those of us trying to bring security to the consumers of these devices.
Hopefully are some lessons to be learned here for future issues and we can get back to making the world safe and secure for consenting users to enjoy.
